- Directed DDOS attacks
- Reflected DDOS attacks
- Amplification attacks
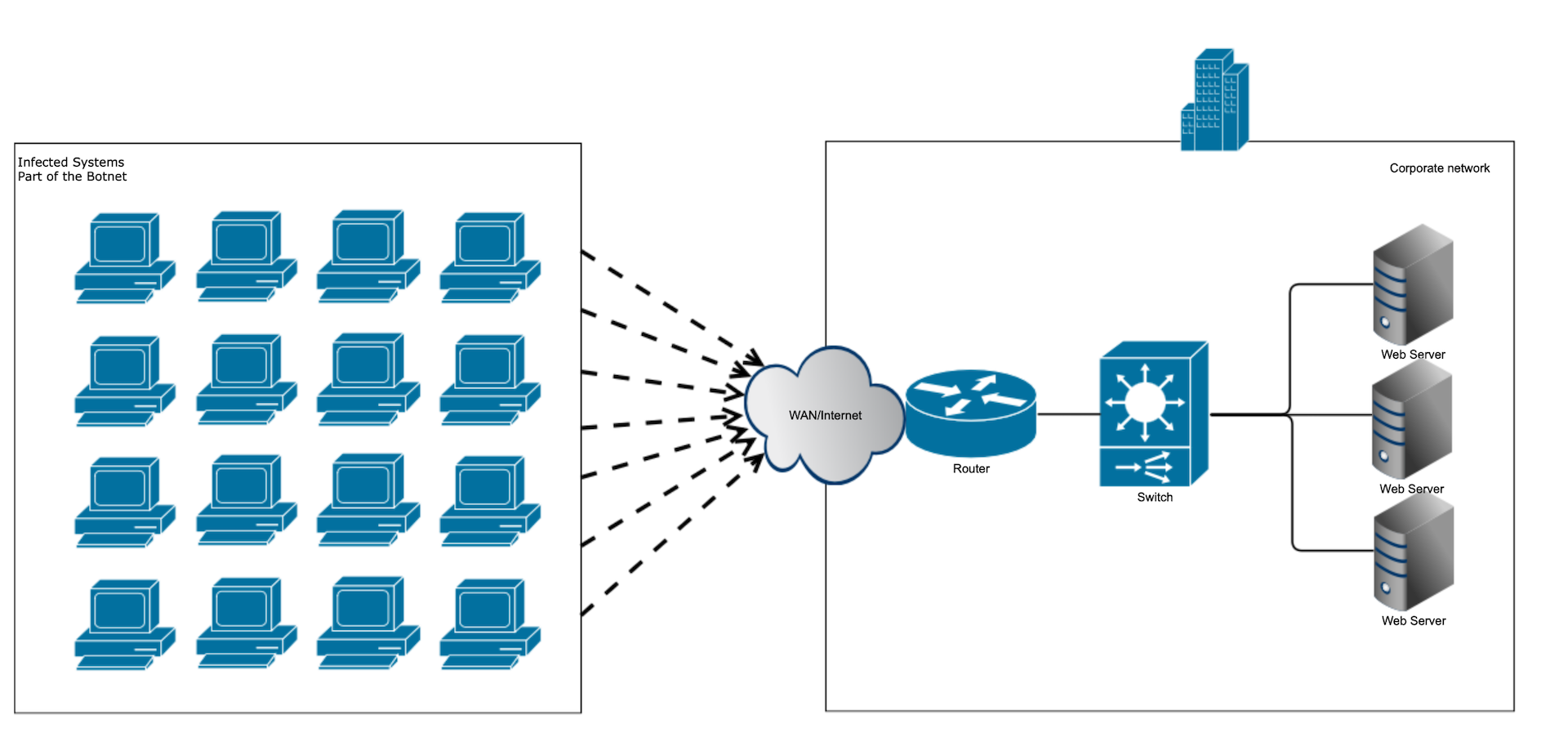
1.2.25.1 Directed DDoS attacks #
directed DDoS attack.
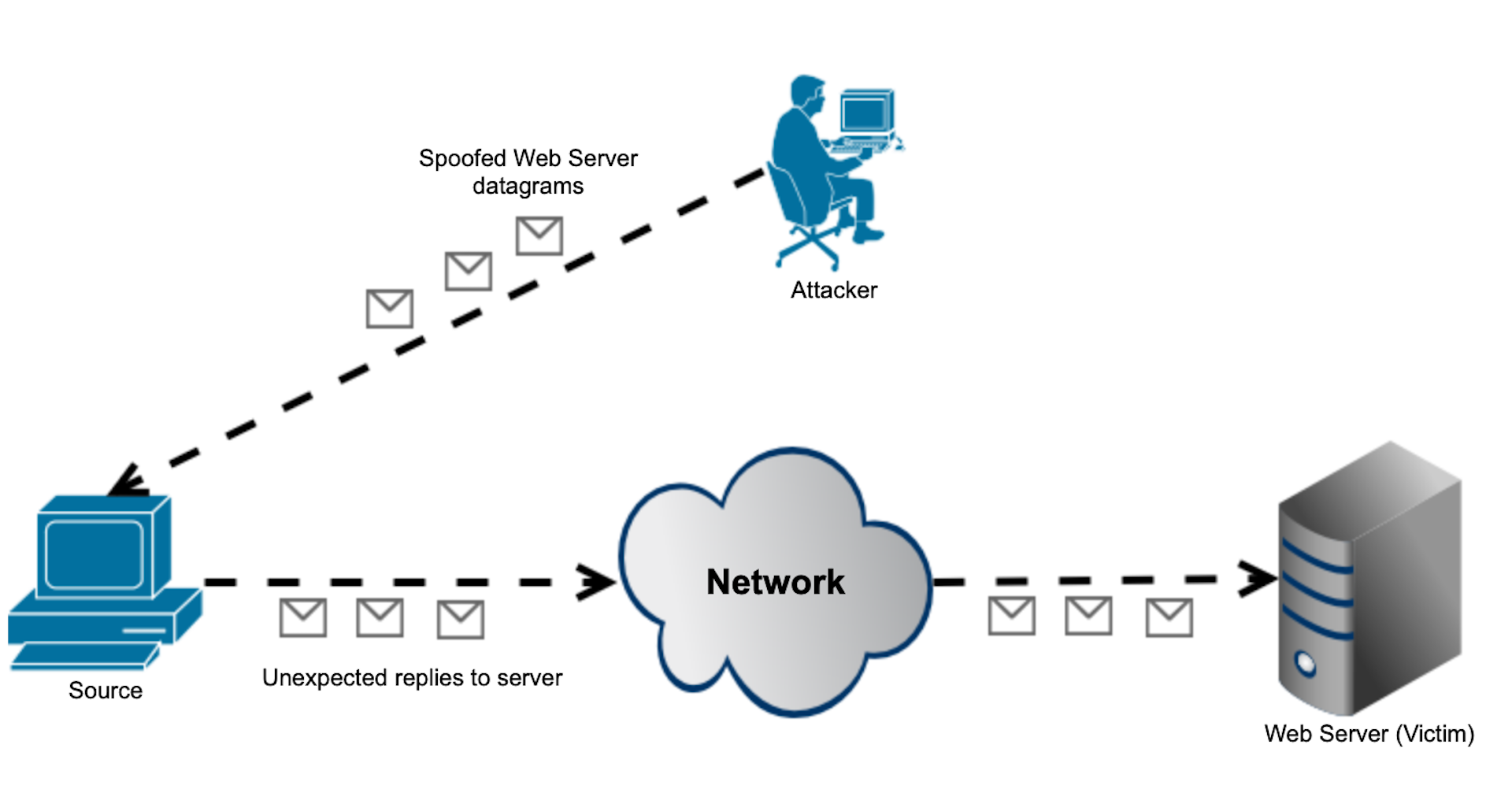
1.2.25.2 Reflected DDOS attacks #
The UDP protocol is easy to use for spoofing as it lacks the 3-way handshake mechanisms. Figure below depicts the typical reflected DDoS attack.
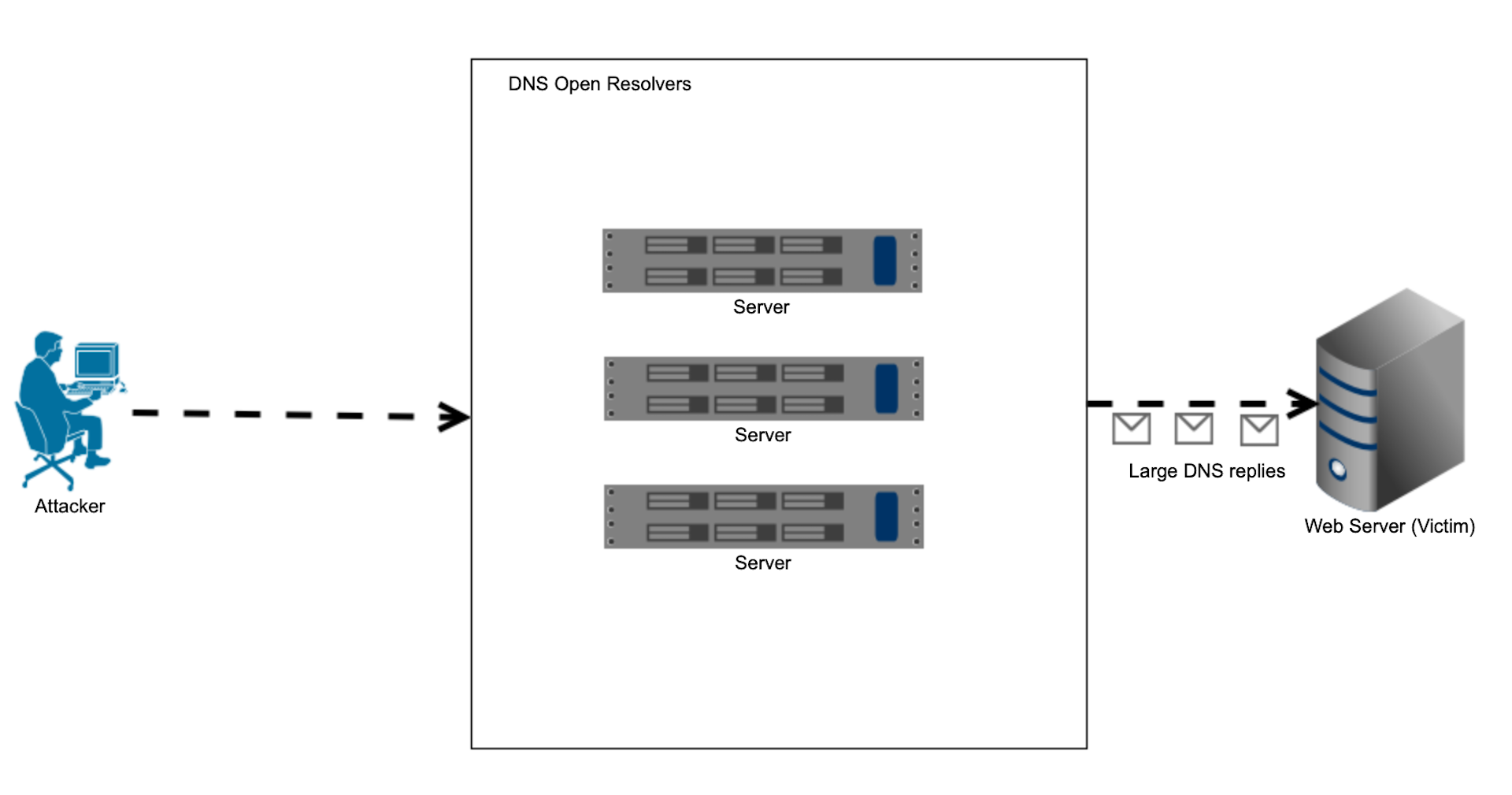
1.2.25.3 Amplification attacks #
are much smaller than replies). As a result, the victim receives a large number of replies, for which it never issues any queries. Figure below depicts the typical amplification DNS DDoS attack.
1.2.25.4 SSH flood attacks #
- Service disruption – legitimate users may be locked out
- Security breach – if a brute force attempt succeeds, the attacker gains access
- Resource exhaustion – server CPU/memory can be drained by handling excessive connections.
- DoS-style flood: The attacker sends a large volume of TCP connection requests to port 22. The goal is to overwhelm the SSH daemon or the server’s network stack. This can slow down or crash the SSH service, preventing legitimate access
- Brute force flood: The attacker rapidly sends multiple SSH login attempts, trying to guess usernames/passwords. These are still TCP connections to port 22, but the focus is on authentication, not just flooding packets
1.2.25.5 DNS amplification attacks #
1.2.25.6 NTP amplification attacks #
1.2.25.7 UDP flood attack #
1.2.25.8 Smurf attacks #
1.2.25.9 SYN flood attacks #
- SYN: The client initiates a connection by sending a SYN (synchronize) packet to the server.
- SYN-ACK: The server acknowledges the request by sending a SYN-ACK (synchronize-acknowledge) packet back to the client.
- ACK: The client responds with an ACK (acknowledge) packet, establishing the connection.
1.2.25.10 ACK flood attacks #
any associated data or established connection, overwhelming the target’s resources and leading to service disruption. In a standard TCP communication, the ACK packet is part of the three-way handshake
process and subsequent data transfer, confirming the successful receipt of data. In an ACK flood attack:
- Flooding with ACK Packets: The attacker sends a deluge of TCP ACK packets to the target system.
- Resource Consumption: Each ACK packet prompts the target’s system to check for a corresponding active session. Since these ACK packets are unsolicited and not part of any established connection,
the system expends resources processing them. - Service Disruption: The excessive processing required for these illegitimate ACK packets can exhaust the target’s resources, leading to degraded performance or complete service unavailability.
packet, even if it’s illegitimate.