Irpflowd is a NetFlow/sFlow collector that receives and analyzes network traffic information, generated by your router(s).- NetFlow – an IP network statistics protocol developed by Cisco Systems, Inc. for collecting and transferring statistics regarding IP traffic information from network devices such as switches/routers to network analysis applications.
Irpflowdcurrently supports the following NetFlow versions: v1, v5, v9.
- sFlow – is a protocol designed for monitoring network, wireless and host devices. Developed by the sFlow.org Consortium, it is supported by a wide range of network devices, as well as software routing and network solutions.
2.7.1.1 Flow agents #
IPv4/interfaceID
peer.X.flow_agents = 8.8.8.8/1 8.8.8.8/2 8.8.8.8/3 8.8.8.8/4
2.7.1.2 TCP port collection for outbound IPs #
The main control for this functionality is the collector.flow.tcp_ports.mode parameter, which defines the port collection method. Depending on the selected mode, the system can either collect ports within a defined range, gather only those listed explicitly, select the lesser port numbers of the one chosen by inbound IP address, or skip port collection entirely. By default, port collection is disabled.
To manage the volume of data, the collector.flow.tcp_ports.limit parameter sets a cap on the number of TCP ports collected per outbound IP address during a one-minute interval. This limit also applies to the Explorer component when determining how many ports to probe for a given IP. The default limit is 5, and values between 1 and 50 are allowed.
When using the range-based collection mode, the start and end of the monitored port range are configured with collector.flow.tcp_ports.min and collector.flow.tcp_ports.max, respectively. By default, the Irpflowd monitors ports from 1 to 3000.
Alternatively, a specific list of TCP ports can be defined using collector.flow.tcp_ports.list, which becomes active when the collection mode is set to “Collect ports in list”.
This functionality ensures that IRP targets relevant and reachable TCP ports when collecting data and performing active measurements, while maintaining efficient data handling through customizable limits
and flexible collection scopes.
2.7.1.3 Configuration #
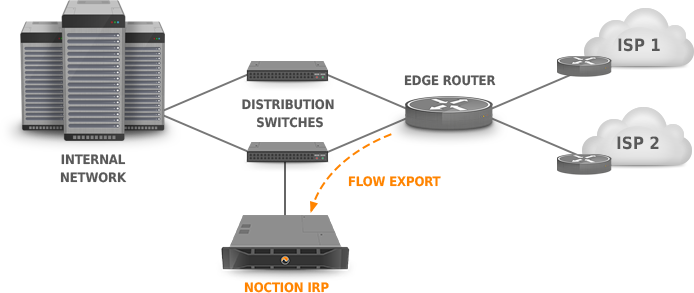
irpflowd collector, the following steps must be completed:- NetFlow/sFlow/jFlow must be configured on the router(s), which must send traffic flow information to the main IRP server IP (Figure Figure: Flow export configuration). See (Vendor-specific NetFlow configuration examples) for specific network device configuration instructions
- Irpflowd must be enabled (by setting the collector.flow.enabled parameter):
collector.flow.enabled = 1
- A list of all the networks, advertised by the edge routers that IRP will optimize, should be added to the configuration. This information should be specified in the collector.ournets parameter.
- For security reasons, the list of valid Flow sending IP addresses must be configured in the collector.flow.sources, to protect
irpflowdfrom unauthorized devices sending Flow data.
Example:
collector.flow.sources = 10.0.0.0/29
- In case the Flow exporters are configured to use non-standard port numbers (
2055for NetFlow/jFlow and6343for sFlow), then collector.flow.listen.nf and collector.flow.listen.sf must be adjusted accordingly:
collector.flow.listen.nf = 2055 collector.flow.listen.sf = 6343
2.7.1.4 Vendor-specific NetFlow configuration examples #
NetFlow configuration on Cisco 7600/6500 series routers #
Listing 2.1: Global MLS settings configuration
(config)# mls netflow (config)# mls flow ip interface-full (config)# mls flow ipv6 interface-full (config)# mls sampling packet-based 512 8192 (config)# mls nde sender version 7
2055 by default)Listing 2.2: Global NetFlow settings and export configuration
(config)# ip flow-cache entries 524288 (config)# ip flow-cache timeout inactive 60 (config)# ip flow-cache timeout active 1 (config)# ip flow-export version 9 (config)# ip flow-export destination 10.11.12.14 2055
Listing 2.3: Per-interface NetFlow settings configuration
(config)# int GigabitEthernet 3/6 (config-if)# mls netflow sampling (config-if)# ip flow ingress
Flexible NetFlow configuration on Cisco 6500 series routers IOS 15.0SY series #
Listing 2.4: Flexible NetFlow monitor configuration
(config)# flow monitor IRP-FLOW-MONITOR (config-flow-monitor)# record platform-original ipv4 full (config-flow-monitor)# exporter IRP-FLOW-EXPORTER (config-flow-monitor)# cache timeout inactive 60 (config-flow-monitor)# cache timeout active 60 (config-flow-monitor)# cache entries 1048576
Listing 2.5: Flexible NetFlow exporter configuration
(config)# flow exporter IRP-FLOW-EXPORTER (config-flow-exporter)# destination 10.11.12.14 (config-flow-exporter)# source Loopback0 (config-flow-exporter)# transport udp 2055 (config-flow-exporter)# template data timeout 120
2055 by default). Also replace the source interface with the actual one.Listing 2.6: Flexible NetFlow sampler configuration
(config)# sampler flow-sampler (config-sampler)# mode random 1 out-of 1024
Listing 2.7: Per-interface Flexible NetFlow settings configuration
(config)# interface FastEthernet0/0 (config-if)# ip flow monitor IRP-FLOW-MONITOR sampler flow-sampler input (config-if)# ip flow monitor IRP-FLOW-MONITOR sampler flow-sampler output
NetFlow configuration on Cisco 7200/3600 series routers #
2055 by default)Listing 2.8: NetFlow configuration on Cisco 7200/3600 series routers
Router(config)# ip flow-cache entries 524288 Router(config)# ip flow-cache timeout inactive 60 Router(config)# ip flow-cache timeout active 1 Router(config)# ip flow-export version 9 Router(config)# ip flow-export destination 10.11.12.14 2055
Ingress/egress flow export configuration on peering interfaces #
Listing 2.9: Ingress/egress flow export configuration on peering interfaces
Router(config)#interface FastEthernet 1/0 Router(config-if)#ip flow ingress Router(config-if)#ip flow egress
Ingress flow export configuration (earlier IOS releases) #
Listing 2.10: Ingress flow export configuration
Router(config)#interface FastEthernet 1/0 Router(config-if)#ip route-cache flow
NetFlow/sFlow configuration examples for Vyatta routers (VC 6.3) #
Listing 2.11: Configuring NetFlow export on Vyatta
vyatta@vyatta# set system flow-accounting netflow server 10.11.12.14 port 2055 vyatta@vyatta# set system flow-accounting netflow version 5
Listing 2.12: Configuration of an interface for the flow accounting
vyatta@vyatta# set system flow-accounting interface eth0 vyatta@vyatta# commit
jFlow export configuration for Juniper routers #
Listing 2.13: Juniper flow export configuration
forwarding-options {
sampling {
input {
family inet {
rate 1000;
}
}
}
family inet {
output {
flow-server 10.10.3.2 {
port 2055;
version 5;
source-address 10.255.255.1;
}
}
}
}
NetFlow export must be configured on all the interfaces facing the providers. In some cases, it may also be necessary to enable NetFlow forwarding on the interfaces facing the internal network.
Listing 2.14: Per-interface NetFlow sampling configuration
interfaces {
xe-0/0/0 {
unit 0 {
family inet {
sampling {
input output;
}
}
}
}
}