 When it comes to distributed denial-of-service (DDoS) attacks, they are far from a downward trend. Although the popularity of certain types of DDoS attacks among cybercriminals varies over the quarters of 2022, the Cloudflare DDoS report for Q3 2022 clearly indicates an overall increase in DDoS attacks compared to last year. For example, HTTP DDoS (application DDoS attack) increased by 111% year-over-year (year-over-year), while network-layer DDoS attacks increased by 97% year-over-year [1].
When it comes to distributed denial-of-service (DDoS) attacks, they are far from a downward trend. Although the popularity of certain types of DDoS attacks among cybercriminals varies over the quarters of 2022, the Cloudflare DDoS report for Q3 2022 clearly indicates an overall increase in DDoS attacks compared to last year. For example, HTTP DDoS (application DDoS attack) increased by 111% year-over-year (year-over-year), while network-layer DDoS attacks increased by 97% year-over-year [1]. In addition, based on a survey reported by Cloudflare customers, DDoS attacks that require a ransom to be paid to stop or avoid the attack increased by 67% year-over-year. Obviously, that ransomware DDoS attacks are increasingly becoming a way for cybercriminals to make money or cause disruption for their own purposes, with governments and financial institutions typically being the main targets.
DDoS mitigation techniques have gradually evolved over time. Older “blackhole” methods, such as the Destination Targeted Remotely Triggered Blackhole (D/RTBH), have proven to be very effective, but the victim’s destination IP address is completely unreachable. The main idea is to move away from penalizing whole prefixes under attack and thereby causing blackholes for “innocent” sessions, but instead, penalize either individual flows or aggregation of DDoS flows. This is where BGP Flowspec (RFC 8955) comes into play, with its ability to more accurately describe DDoS traffic along with the automatic rule distribution.
In BGP-FS, flowspec or “firewall” rule consists of traffic description and action. The example of traffic description is a source address 192.168.1.1/32, protocol ICMP, and the destination address 192.168.2.1/32 (Figure 1). The action is set to drop traffic. The rule is configured on a flowspec controller (router P) and distributed inside the BGP update message to flowspec clients (PE2 and PE1). Both clients receive this rule from the controller and program the match/actions in hardware. ICMP flood from Attacker (190.160.1.1) to Server (190.160.2.1) received on the edge router PE1 matching the description will be dropped, while ICMP echo request from host 190.160.1.2 to Server forwarded.
ICMP flooding is a type of Layer 3 and Layer 4 DDoS attacks, which in turn are volumetric DDoS attacks. Other volumetric DDoS attacks, such as amplification attacks, take advantage of vulnerable services like Memcached, NTP, DNS, etc., running on public servers on the Internet. The attacker launches multiple spoofed queries to servers that will flood the victim with large reply packets, filling up links and, in many cases, resulting in the target network infrastructure collapsing.
Volumetric DDoS attacks do not need to be handled by a sophisticated scrubbing system to be mitigated but must be filtered at the edge routers (BGP-FS clients). BGP-FS allows such traffic to be accurately matched against Layer 3 and Layer 4 parameters. Malicious traffic is filtered at the edge of the network so that the provider’s core network and its customers are not impacted by the huge volume of traffic. However, in the case of mitigating stateful DDoS attacks, a different approach must be used, which is to redirect traffic to a DDoS mitigation device.
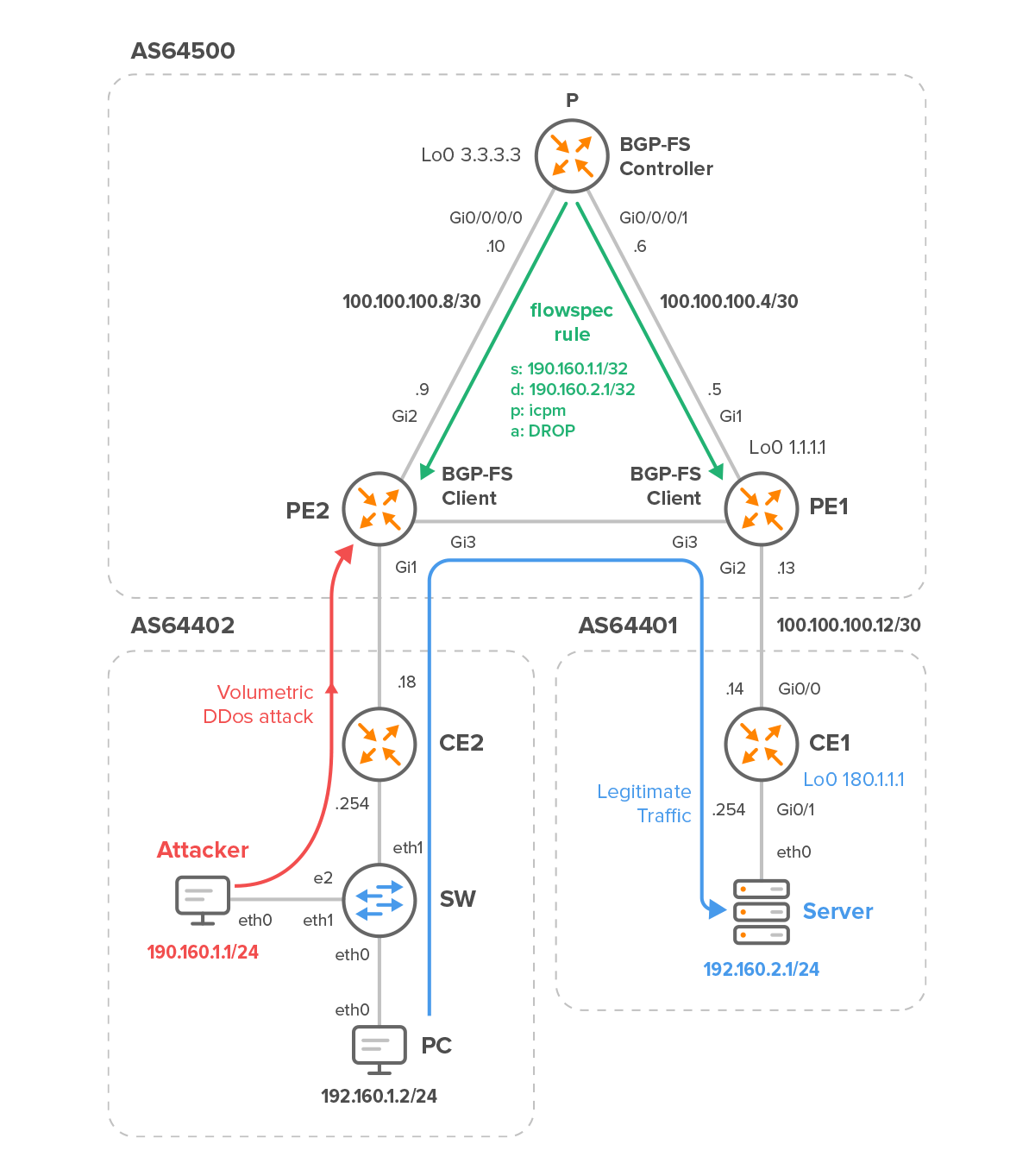
Figure 1 – Volumetric DDoS from the Attacker Dropped on PE2
Stateful DDoS attacks cannot be stopped by BGP-FS clients alone and need to be addressed by a DDoS scrubbing device. For example, in the case of a TCP SYN flood attack, BGP-FS does not possess the required intelligence to figure out which TCP SYN packet is harmful and vice versa. Flowspec just inspects traffic in one direction, but we need to examine if there is an appropriate SYN+ACK response from the server to determine if the TCP SYN packet is legitimate or not.
Instead of setting BGP-FS action to rate limit traffic to zero on edge routers, we will use BGP-FS to redirect a specific “flow” to a DDoS scrubbing appliance, e.g., packets with the destination IP address of the victim and destination TCP port 80. BGP-FS can be used to program different actions:
- Diversion to a different VRF
- Diversion to a next-hop address
The role of a scrubbing appliance is to provide a sort of deep packet inspection tool that scrubs out attack traffic and then passes the legitimate traffic on to customers.
Redirecting DDoS Traffic to Scrubbing Appliance via VRF Routing Instance
The BGP-FS controller advertises flowspec route with source address 190.160.1.1 to 190.160.2.1, the destination TCP port 80 (Figure 2). The extended community “redirect to VRF” is attached to flowspec route with the route target that corresponds to the VRF route target configured on the edge router PE2.
Traffic received on the ingress interface Gi1 on PE2 matching flowspec route is redirected from the global routing table (GRT) to VRF via egress interface G4 (red line). The default route configured for the VRF on PE2 punts all traffic directly to the scrubbing appliance. Suspected traffic is analyzed here, and the clean traffic is routed back to PE2 via G0/1.
In order to exclude the Gi5 interface from flowspec processing and avoid a routing loop, flowspec must be disabled on this interface on the PE2 device. This will allow return traffic from the scrubber to PE2 to flow eastbound towards PE1 inside GRT.
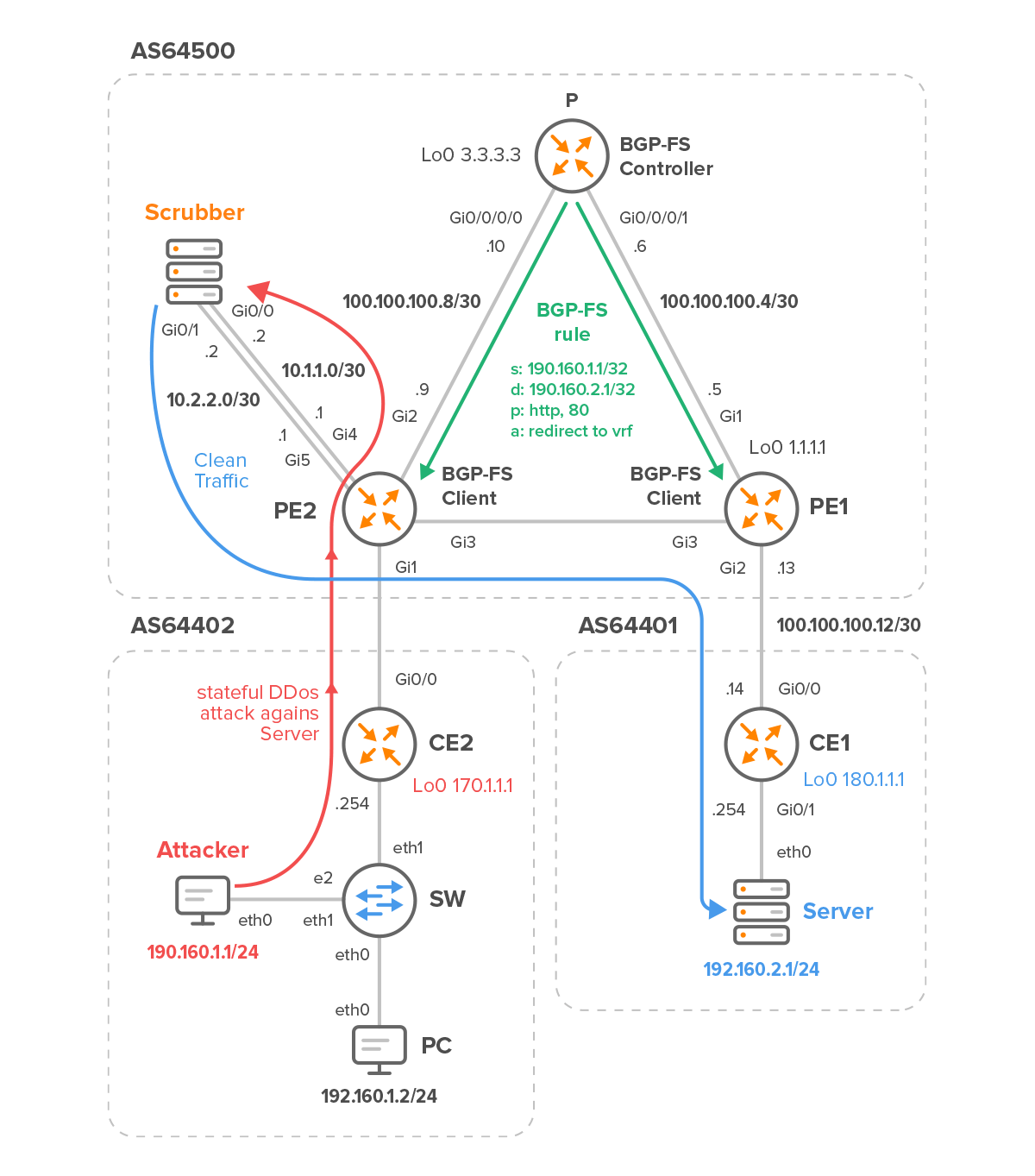
Figure 2 – Stateful DDoS redirected to Scrubbing Appliance via VRF on PE2
Redirecting DDoS Traffic to Scrubbing Appliance via IPv4/IPv6 Next-Hop
For the purpose of redirecting/mirroring traffic to IP next-hop, the IETF draft proposes a new extended community 0x0800. The draft provides a simpler method of policy-based forwarding in networks without L3 VPNs.
Clients that install the flowspec route should redirect the corresponding packets to the new next-hop address, which is the IP address of the scrubbing appliance. The dirty traffic received on the ingress interface Gi1 of client PE2 and matching flowspec route is redirected to the scrubbing device address 10.1.1.2 via interface G4 within GRT (Figure 2). The scrubbing appliance redirects clean traffic to PE2 via G0/1 towards Server 190.160.2.1.
To avoid the routing loop, BGP-FS must be disabled on the Gi5 interface of PE2. The configured next-hop address 10.1.1.2 must be reachable on the flowspec controller; otherwise, the rule is not advertised to clients.
Conclusion:
BGP-FS is certainly not a one-size-fits-all tool to mitigate all types of DDoS attacks, as it is not intelligent enough to filter out malicious traffic from legitimate traffic when they have similar characteristics. However, it can be used to define redirect-to-VRF or redirect-to-next-hop actions so that we can redirect suspicious network traffic to a DDoS mitigation device.
BGP-FS also optimizes the benefits of scrubbing appliances since it provides precise diversion of selected traffic either on demand or continuously per application. This enables better optimization of the shared mitigation capacity of the mitigation appliance.
By any means, BGP-FS is a great technology that improves response time to mitigate DDoS attacks because ACL distribution is simplified and controlled from one central point. The big advantage of Flowspec is also that this is all done directly in hardware. There is virtually no performance hit, even with small packets thus, we should be able to run flowspec rules at line speed.
Those are the reasons why large-scale providers successfully leverage flowspec as part of their DDoS mitigation toolset.
To automate your network’s DDoS detection and mitigation actions, consider looking at the latest Noction Intelligent Routing Platform version featuring the FlowSpec Redirect and BGP redirect threat mitigation mechanisms.