This tutorial discusses the configuration of a multihomed enterprise network where routers CE-1 and CE-2 in AS 64501 are connected to routers ISP-A in AS64500 and ISP-B in AS64502 for redundancy. The connection via ISP-A is used as a primary connection for both outbound and inbound traffic. The connection via ISP-B is a backup connection. Identical inside hosts behind NAT are translated to different addresses assigned by the respective ISPs depending on whether traffic is forwarded via ISP-A or ISP-B to the Internet.
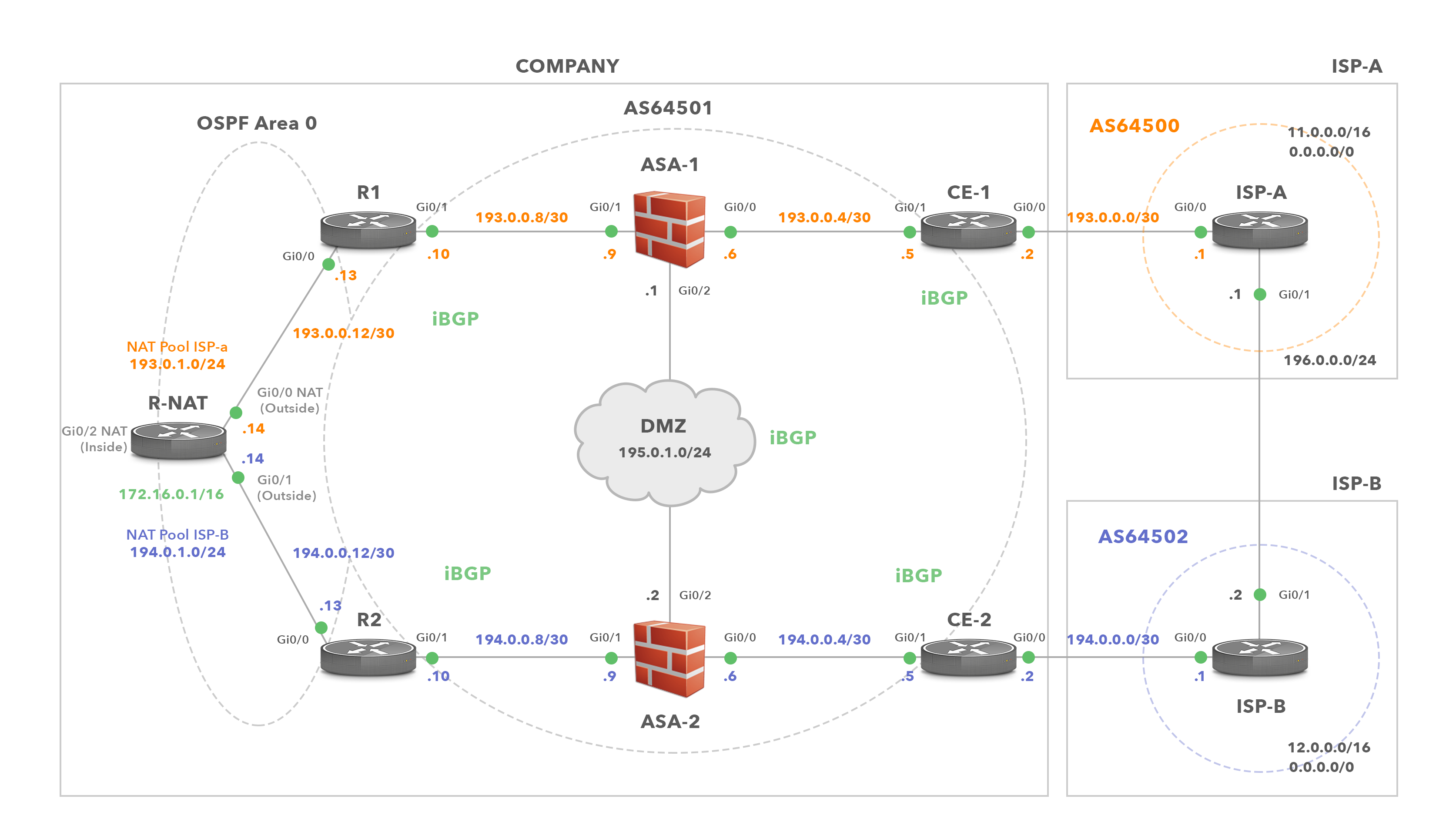
Diagram 1: Enterprise Network (AS64501) is Multi-homed to ISP-A and ISP-B
Let’s go through every line of our configuration to explain its purpose. Below are the rules for outbound traffic from the enterprise to the Internet.
- All outbound traffic from 172.16.0.0/16 forwarded from R-NAT to R1 router has an inside global IP addresses assigned from the 193.0.1.0/24.
- All outbound traffic from 172.16.0.0/16 forwarded to R2 router has an inside global IP address assigned from the 194.0.1.0/24.
- AS64501 prefers the path from CE-1 to ISP-A for outbound traffic. Hence, a preferred outbound path for traffic sent from hosts behind NAT into the Internet is R-NAT→R1→ASA-1→CE-1→ISP-A. We give this path the name nat-north-internet. NAT pool 193.0.1.0/24 is used for mapping the inside local addressees (172.16.0.0/16) to the inside global addresses when the nat-north-internet path is taken.
- DMZ prefers a path via ASA-1, CE-1 and ISP-A for outbound traffic to the Internet. The path’s name is dmz-north-internet path.
- If connectivity to ISP-A fails, all outbound traffic from hosts behind NAT is forwarded via a link from CE-2 to ISP-B. Therefore, it takes the path R-NAT→R2→ASA-2→CE-2→ISP-B, aka nat-south-internet path. The NAT pool 194.0.1.0/24 is used for mapping the inside local addresses to the inside global addresses in this case.
- If connectivity to ISP-A fails, all outbound traffic from hosts in DMZ to the Internet is routed via a link from CE-2 to ISP-B. In this case, traffic is forwarded to ASA-2→CE-2→ISP-B, via the dmz-south-internet path.
Here are the rules for inbound traffic.
- All inbound traffic that comes from the Internet to the enterprise uses the link from ISP-A to CE-1. This traffic is destined either for hosts in DMZ or for NAT pool 193.0.1.0/24 (translated local inside IP addresses 172.16.0.0/16).
- If a link from ISP-A to CE-1 fails, all inbound traffic from the Internet is routed via the link from ISP-B to CE-2. This traffic is destined either for DMZ or for NAT pool 194.0.1.0/24.
IP Addresses Assignment:
The enterprise has received a prefix from each ISP. These are used for NAT and interfaces configuration (Picture 1). In addition, the enterprise has also assigned the prefix 195.0.1.0/24 to be used for DMZ configuration. The prefix 193.0.0.0/23 is assigned from ISP-A. This prefix consists of two /24 subnets – 193.0.0.0 and 193.0.1.0. The company uses the subnet 193.0.0.0/24 for IP address configuration of devices located on the north path (R1, ASA-1 and CE-1). The prefix 193.0.1.0/24 is reserved for NAT pool ISP-A. The enterprise has assigned the prefix 194.0.0.0/23 from ISP-B. The 194.0.0.0/24 subnet has been allocated for the south path configuration (R2, ASA-2 and CE-2). The prefix 194.0.1.0/24 is reserved for NAT pool ISP-B.
Prefix Advertisement and Path Selection
The IP address range 195.0.1.0/24 is used for IP address configuration of devices in DMZ. The prefix is advertised by routers CE-1 and CE-2 via eBGP to ISP-A and ISP-B, respectively. However, since the dmz-north-internet path is preferred over the dmz-south-internet for the outbound traffic from DMZ to the Internet, we set a local preference to 150 for a default route 0.0.0.0/0 via CE-1. It effectively makes the path via CE-1 preferred as the default local preference is 100 for a default route installed in the routing table of CE-2.
The prefix for NAT 193.0.1.0/24 is announced solely by CE-1 in an eBGP update to the ISP-A and from ISP-A into the Internet. As CE-1 is the only router advertising this prefix, the inbound traffic sent from the Internet to the NAT prefix 193.0.1.0/24 takes the internet-north-nat path. The inbound traffic destined for the DMZ 195.0.1.0/24 is also routed via ISP-A to CE-1 and ASA-1 (internet-north-dmz path). The path via ISP-A gets selected by BGP routers located in the other ASs because CE-2 is configured to prepend as-path three times with its own AS 64501 for the DMZ route 195.0.1.0/24 advertised to CE-2. Therefore, the shorter AS_PATH via ISP-A is preferred.
If a link between CE-1 and ISP-A fails, the 193.0.1.0/24 prefix is not advertised by AS64501 at all. It might seem to be a design mistake at first, however when that link fails, the path nat-north-internet is not being used anymore. Instead, outbound traffic from R-NAT to ISP-B is routed via nat-south-internet path with the source IP addresses translated to the pool NAT 194.0.1.0/24. As the prefix 194.0.1.0/24 is advertised by CE-2, the devices behind NAT can communicate with devices in the Internet.
| Note: Routers CE-1 and CE-2 contain the full Internet routing table. The Internet routes are simulated by prefixes 11.0.0.0/16 and 12.0.0./16 advertised by ISPs via an eBGP update to CE routers. |
Default Route Distribution
We have already mentioned that if a link between ISP-A and CE-1 fails, outbound traffic from devices behind NAT into the Internet is routed via a backup path nat-south-internet. But how does this magic work? Both CE-1 and CE-2 advertise a default route to R1 and R2 in an iBGP update message, respectively. However, they do it conditionally as they advertise a default route only if there is an appropriate route (11.0.0.0/16 for ISP-A and 12.0.0.0/16 for ISP-B) along with the ISP’s IP address as a next-hop installed in their routing table. If not, CE routers do not advertise a default route to R1, R2 and DMZ.
Routers R1 and R2 advertise a default route to R-NAT conditionally, based on the links between CE and ISP routers being active. For instance, if R1 receives a default route via iBGP from CE-1 it installs it into its routing table. If the route-map CHECK-DEFAULT matches a default route and the next-hop IP address (CE-1), R1 advertises it via OSPF to R1, with the metric 5. R2, however advertises a default route (if the link between CE-2 and ISP-B is active) via OSPF to R-NAT with the metric 30. As a result, R-NAT installs a default route received from R1 with the metric 5 since it is lower than metric 30 of the default route advertised by R2.
Adjusting Administrative Distance (AD) for iBGP learned Default Route on R1
For the iBGP routes with a default AD value 200 to be prefered over OSPF routes with a default AD value 110, we need to change the AD of iBGP routes bellow 110. If we use the command distance 20 105 200 under the BGP configuration of R1, a default route with AD 105 received from CE-1 in an iBGP update message has an AD lower than 110. The AD of a default route advertised by R-NAT from R2 is 110. Therefore, R1 installs a route 0.0.0.0 via CE-1 into its routing table.
If a link between CE-1 and ISP-1 goes down, R-NAT installs a default route with AD 110 and metric 30 advertised by R2 via OSPF. R1 also installs a default route received from R-NAT into its routing table. Outbound traffic is then sent to ISP-B. If the link between CE-1 and ISP-A goes up, a default route via CE-1 will be reinstalled into the routing table of R1.. The AD of this route is 105 thus it will be preferred to a default route with AD 110 advertised by R-NAT. Outbound traffic will be routed via ISP-A again.
| Note: The default values of the command distance are bgp 20 200 200. The eBGP-learned routes have an administrative distance of 20, iBGP-learned routes have an administrative distance of 200, and local BGP routes have an administrative distance of 200. |
R-NAT Configuration
NAT Configuration
AS64501 is multi-homed, connected to ISP-A and ISP-B for redundancy. We use subnet 193.0.1.0/24 for mapping the inside local addresses to the inside global addresses when outbound traffic from inside hosts is routed via R1. Similarly, the subnet 194.0.1.0/24 is used for translation when outbound traffic from the inside host is routed via R2. Therefore, we have created two NAT pools – 193.0.1.0/24 and 194.0.1.0/24, one for each ISP respectively. The same local inside address from the subnet 172.16.0.0/16 will be translated to different inside global address available in ISP-A and ISP-B NAT pools.
We also implement the pools overload. It means that the first address from the pool and port is to be used. Once all ports are exhausted, the second address from the pool will be used as an inside global address, etc. In theory, up to 65535 inside local addresses could be mapped to a single inside global address (based on the 16-bit port number). This type of NAT is called Dynamic NAT.
Router R-NAT has been configured with the IP address 172.16.0.1/16 on the GigabitEthernet0/2 interface. It is the subnet from a private IPv4 address space (RFC1918) that is going to be translated to NAT pools. Hosts located behind NAT have their IP addresses assigned from this address range. Therefore, we need to tell R-NAT that the interface Gi0/2 is located within the inside network. We will do it with the command ip nat inside.
interface GigabitEthernet0/2 description LAN interface ip address 172.16.0.1 255.255.0.0 ip nat inside
The interfaces GigabitEthernet0/0 and 0/1 are located in the outside network thus we configure them as the outside interfaces with the command ip nat outside.
interface GigabitEthernet0/0 description Link to R1 ip address 193.0.0.14 255.255.255.252 ip nat outside interface GigabitEthernet0/1 description Link to R2 ip address 194.0.0.14 255.255.255.252 ip nat outside
Let’s configure NAT pools. The NAT pool ISP-A contains addresses assigned by ISP-A. The ISP-B pool contains IP addresses assigned by ISP-B.
ip nat pool ISP-A 193.0.1.1 193.0.1.254 netmask 255.255.255.0 ip nat pool ISP-B 194.0.1.1 194.0.1.254 netmask 255.255.255.0
The line below configures a Dynamic NAT mapping of the inside network 172.16.0.0/16 to a global address from the pool ISP-A. Inside addresses are matched by the route-map ISP-A.
ip nat inside source route-map ISP-A pool ISP-A overload
We will do the same for ISP-B pool.
ip nat inside source route-map ISP-B pool ISP-B overload
Let’s create a route-map ISP-A. It matches all traffic matched by the access-list (ACL) NAT and going out of the interface Gi0/0.
route-map ISP-A permit 10 match ip address NAT match interface GigabitEthernet0/0
The route-map ISP-B matches all traffic matched by ACL NAT and going out of interface Gi0/1.
route-map ISP-B permit 10 match ip address NAT match interface GigabitEthernet0/1
Finally, we create the ACL NAT which is the named source ACL matching traffic from all hosts in the inside network.
ip access-list standard NAT permit 172.16.0.0 0.0.255.255
OSPF Configuration
R-NAT router is running OSPF and forms OSPF adjacency with routers R1 and R2. Therefore, we must advertise the subnets 193.0.0.12/30 and 194.0.0.12/30. The OSPF point-to-point network type must be configured for both loopback interfaces, otherwise the NAT networks will be advertised as host networks with prefix length /32.
interface Loopback0 ip address 193.0.1.1 255.255.255.0 ip ospf network point-to-point interface Loopback1 ip address 194.0.1.1 255.255.255.0 ip ospf network point-to-point
Let’s also implement the inter-area filtering on R-NAT to prevent routes from other areas being advertised into the area 0. 0.0.0.0/0 le 32 matches any prefix with a length between 0 and 32 bits (inclusive). This matches all possible IPv4 prefixes.
router ospf 1 area 0 filter-list prefix ADV-TO-R in network 193.0.0.12 0.0.0.3 area 0 network 193.0.1.0 0.0.0.255 area 0 network 194.0.0.12 0.0.0.3 area 0 network 194.0.1.0 0.0.0.255 area 0 ip prefix-list ADV-TO-R seq 999 deny 0.0.0.0/0 le 32
R1 and R2 Configuration
R1 Configuration
interface GigabitEthernet0/0 description Link to R-NAT ip address 193.0.0.13 255.255.255.252 interface GigabitEthernet0/1 description Link to ASA-1 ip address 193.0.0.10 255.255.255.252
Now let’s configure OSPF to advertise a default route conditionally, based on whether the link between CE-1 and ISP-1 is active, with the metric 5. Hence, R-NAT will prefer the route via R1 for outgoing traffic to the default route learned via OSPF from R2, with metric 30.
router ospf 1 network 193.0.0.12 0.0.0.3 area 0 default-information originate metric 5 route-map CHECK-DEFAULT
The R1 router is an iBGP peer with the routers CE-1 and DMZ. The bgp redistribute-internal command can be used as a workaround here. Without this command, even though R1 has a default route with the next-hop 193.0.0.5 learned via iBGP installed in the routing table, a default route is not advertised to R-NAT.
The redistribution of OSPF routes into iBGP is done with the help of the redistribute ospf 1 command. The command distance bgp 20 105 200 changes the default AD from 200 to 105 for routes learned via iBGP.
router bgp 64501 bgp log-neighbor-changes bgp redistribute-internal redistribute ospf 1 neighbor 193.0.0.5 remote-as 64501 neighbor 193.0.0.5 next-hop-self neighbor 195.0.1.3 remote-as 64501 neighbor 195.0.1.3 next-hop-self distance bgp 20 105 200
Now we need static routes to iBGP peers as they are not directly connected.
ip route 193.0.0.4 255.255.255.252 193.0.0.9 ip route 195.0.1.3 255.255.255.255 193.0.0.9 route-map CHECK-DEFAULT permit 10 match ip address 30 match ip next-hop 31 access-list 30 permit 0.0.0.0 access-list 31 permit 193.0.0.5
R2 Configuration
interface GigabitEthernet0/0 description Link to R-NAT ip address 194.0.0.13 255.255.255.252 interface GigabitEthernet0/1 description Link to ASA-2 ip address 194.0.0.10 255.255.255.252
We will configure OSPF to advertise a default route conditionally, based on whether the link between CE-1 and ISP-1 is active, with the metric 30.
router ospf 1 network 194.0.0.12 0.0.0.3 area 0 default-information originate metric 30 route-map CHECK-DEFAULT
The R2 router is an iBGP peer with the routers CE-2 and DMZ. The command redistribute ospf 1 redistributes OSPF routes into iBGP.
router bgp 64501 bgp log-neighbor-changes bgp redistribute-internal redistribute ospf 1 neighbor 194.0.0.5 remote-as 64501 neighbor 194.0.0.5 next-hop-self neighbor 195.0.1.3 remote-as 64501 neighbor 195.0.1.3 next-hop-self
We need static routes to iBGP peers as they are not directly connected.
ip route 194.0.0.4 255.255.255.252 194.0.0.9 ip route 195.0.1.3 255.255.255.255 194.0.0.9 route-map CHECK-DEFAULT permit 10 match ip address 30 match ip next-hop 31 access-list 30 permit 0.0.0.0 access-list 31 permit 194.0.0.5