When it comes to distributed denial-of-service (DDoS) attacks, they are far from a downward trend. Although the...
Noction Blog
The latest BGP network optimization and IP flow analysis trends.
Optimizing BGP convergence
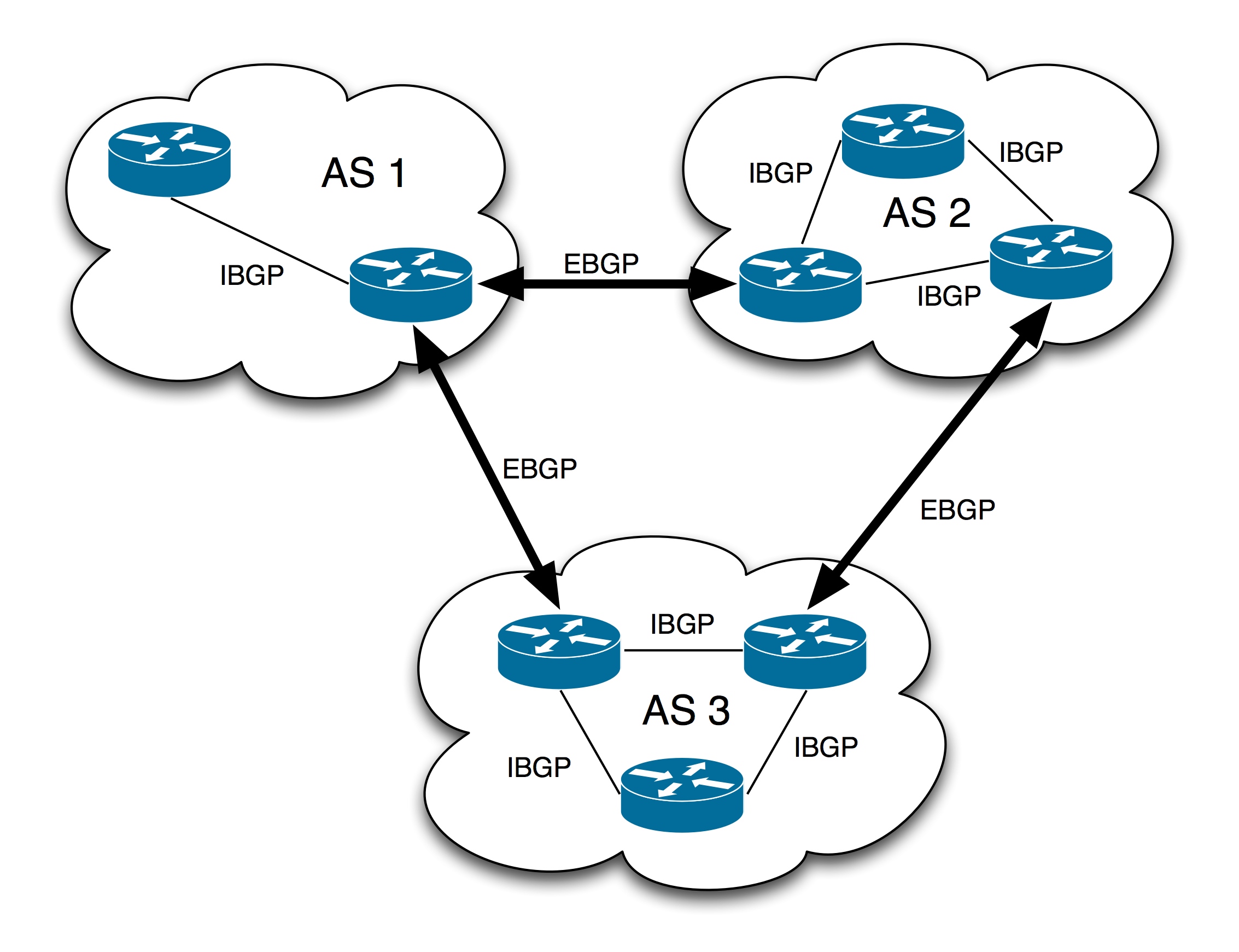
When there is a change in the reachability of one or more prefixes, BGP needs to do some work to adapt to that change...
SUBSCRIBE TO OUR NEWSLETTER
Is BGP multi-homing enough for WAN network performance?
BGP multihoming has become as necessary to the networks connected to Internet, as the use of redundant power sources...
Network congestion technical implications
During the transfer of information in the Internet, there are various situations related to certain host or network...