 Bring Your Own Device (BYOD) is a practice that allows users to bring their personal devices such as tablets or smartphones to the workplace and use them to access the company’s network. BYOD’s advocates claim that the BYOD trend movement helps to improve productivity, increase employee satisfaction and leads to cost savings. This is achieved by flexible working hours when employees access information when and where they need using a device they can handle better. Therefore, the time the IT team spends on end-user device support and troubleshooting is reduced. Furthermore, a device cost is transferred to employees.
Bring Your Own Device (BYOD) is a practice that allows users to bring their personal devices such as tablets or smartphones to the workplace and use them to access the company’s network. BYOD’s advocates claim that the BYOD trend movement helps to improve productivity, increase employee satisfaction and leads to cost savings. This is achieved by flexible working hours when employees access information when and where they need using a device they can handle better. Therefore, the time the IT team spends on end-user device support and troubleshooting is reduced. Furthermore, a device cost is transferred to employees.
Regardless of the above statements are true or false, the BYOD and enterprise mobility market size is estimated to grow from $72.7 Billion in 2024 to $133.9 Billion by 2029 [1]. Up to 82% of organizations currently have some sort of BYOD program in place [2]. In other words, the practice of bringing iPhones, Androids to a workplace is accepted by more and more companies and this trend has a significant impact on business. As a matter of fact, it is almost impossible to prevent employees to bring their devices to a workplace unless they work for an organization where the usage of BYOD devices is strictly prohibited, such as in the military. As it happens anyway with the vulnerabilities to cyber attack or unintended malware infection being introduced, organizations should take a proactive and informed approach to BYOD. This way they will be prepared to face challenges that the trend of BYOD adoption, implementation and usage brings. NetFlow is of great help here, reducing the negative impact of BYOD on enterprise security and bandwidth consumption.
The major security concerns that come from BYOD device usage include a vanishing perimeter, malware infection and data loss. Typically, devices provided by the company are under the control of an IT department. They provide patch management, create and implement security policies, install and configure antivirus and other software from the list of approved applications. BYOD devices, however, may run various applications infected with malware, even when they are downloaded from an official store. For instance, there are hundreds of Android apps in the Google store that contain Windows malware [3]. Imagine a situation when children download and install such applications into a parent’s tablet. If the tablet is used to access company data locally via a wireless network or remotely using VPN tunnels, malware can be unintentionally transferred to the company’s network. In this case, a network perimeter, highly secured by firewalls and IDS/IPS devices practically disappears as malware enters the company network. This is mostly true in case of BOYD devices connected via a wireless LAN as it is expensive to implement IDS/IPS in the access layer to stop internal malware. Furthermore, if the BYOD device is lost or stolen and no encryption is used, sensitive business data may be put in danger. These devices can be also used to connect to the company’s network remotely over VPN.
Although NetFlow alone cannot handle security challenges, it can be used to identify and monitor BOYD traffic. Being an excellent real-time source of traffic information, it provides knowledge of source and destination IP address (who), source and destination TCP/UDP ports (what), flow start and end (when), packets and bytes counters (how), input and output interfaces (where). NetFlow reports information such as top N talkers for a BYOD subnet and applications that can be used to find how much load BYOD adds to the network bandwidth. Thanks to this, QoS policies can be put in place so business traffic would be prioritized over non-business traffic. In fact, without the ability to reliably identify BYOD devices, it would be hard to enforce QoS policies. In this case, an excessive BYOD traffic generated by bandwidth-greedy applications, video, voice streaming communications, and large file downloads could easily saturate the available bandwidth. Remember, most BYOD devices access the company’s network over an existing wireless infrastructure with limited bandwidth capabilities due to the nature of wireless transmission media.
Monitoring BYOD devices should start on an access layer (Picture 1). This layer is the closest to the source of the local BYOD traffic. Modern versions of NetFlow such as Flexible Netflow allows tracking L2 information such as source and destination MAC addresses, VLAN ID etc.[4] It is very important to collect and export flows with a MAC address of a BYOD device connected to the enterprise network. Typically, IT staff has no control over BYOD devices so changing an IP address can be a matter of a few clicks for a common user. Unlike, the IP address a change of MAC address is not a trivial task and requires deeper technical knowledge. Moreover, a MAC address represents a unique 12-characters (48 bits) host identifier. So far, all produced network devices have been created with unique MAC addresses. The first half of a MAC address (6 characters) encodes a vendor (OUI) and the second half of the MAC address identifies a concrete host (NIC).
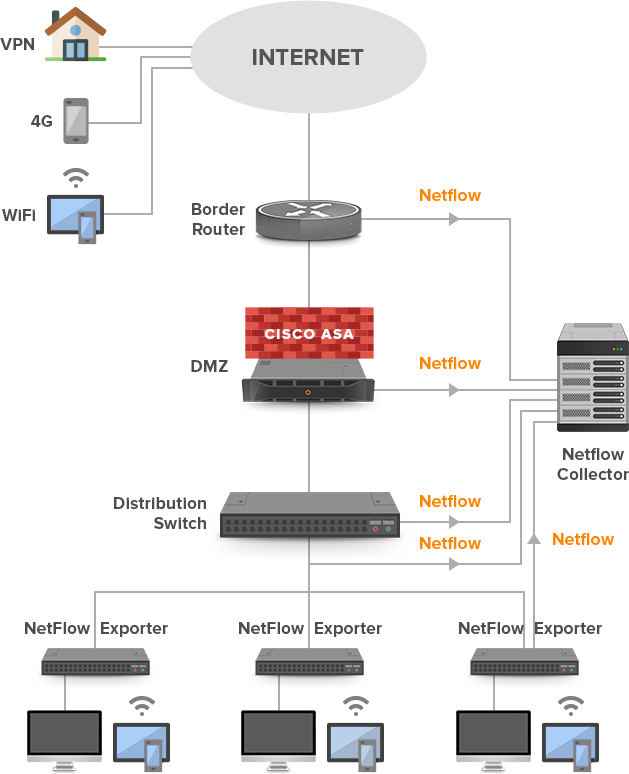
Picture 1: Tracking Local BYOD Devices Connected to Access Layer and Remote BYOD Devices Connected to Corporate Network via the Internet
The content of the flow cache with three flow records is depicted in Picture 2. The host with the highest flow number 365 and MAC address 7C:C5:37:a1:00:01 is the Apple iPhone. The overall packet per flow ratio is only 1.25. This makes us think that the host is involved in some suspicious activity e.g. scanning of the IP network to detect available hosts or certain services. However, confirmation of such activity requires further investigation based on the detailed flow records.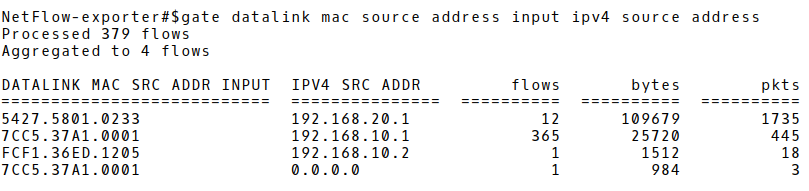
Picture 2: Flow Cache with Three Records
Conclusion:
Identification of BYOD devices based on MAC and IP address is the old but still valid method of tracking hosts. Ideally, a NetFlow exporter should be able to export username and password used for login to a wireless network along with a pair of the IP and MAC address. If not, logs from the Active directory containing a username must be correlated with the information gathered from the NetFlow records.