IRP for Cloud setup: Step by Step
IRP for Cloud satellite VM
IRP for Cloud service is enabled by a satellite VM running in a customer’s VPC and automating the service.
The following apply:
- available on the Marketplace
- requires access keys so that it is able to
- request and install a Virtual Interface/Gateway
- enable Route propagation from IRP for Cloud service
- monitor VPC operation and update IRP for Cloud with changes
- restore to previous configuration in case of incidents
| Note: Access keys never leave satellite VM which is fully under your control and thus third parties not even IRP for Cloud can make any use of them. |
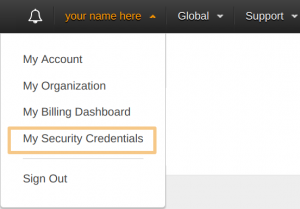
Access keys
Access keys are managed under My Security Credentials:
Access keys are required to automate IRP for Cloud and other services. Refer your cloud provider documentation for further details.
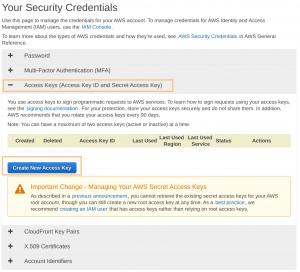
| Note: Cloud providers impose a limit on the number of active Access Keys. |
Create New Access Key or retrieve an existing set.
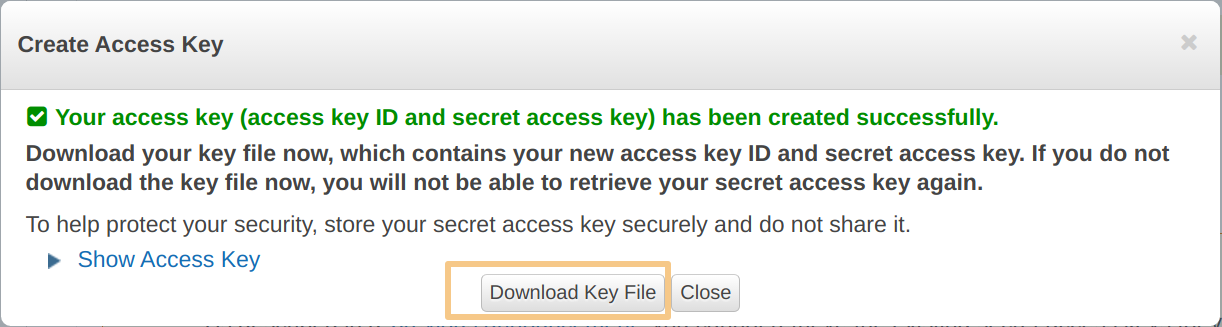
A file will download. For example in the case of AWS a rootkey.csv file is returned:
| Note: Please store the access key file in a secure location! |
Open the access key file with a textual editor for example Gedit or Notepad.
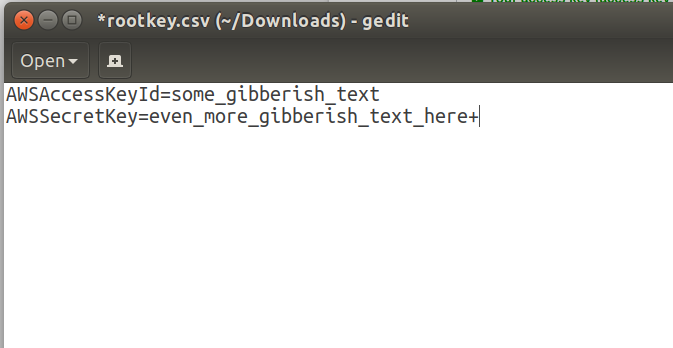
| Note: Just clicking on the file might open it with a spreadsheet application due to the default file extension set to the file. |
Launch IRP for Cloud satellite VM instance with access key ready
Launch the AMI from Marketplace and in the Launch Wizard at step 3 provide the access key from the saved file. Feel free to use copy/paste from the text editor of choice.
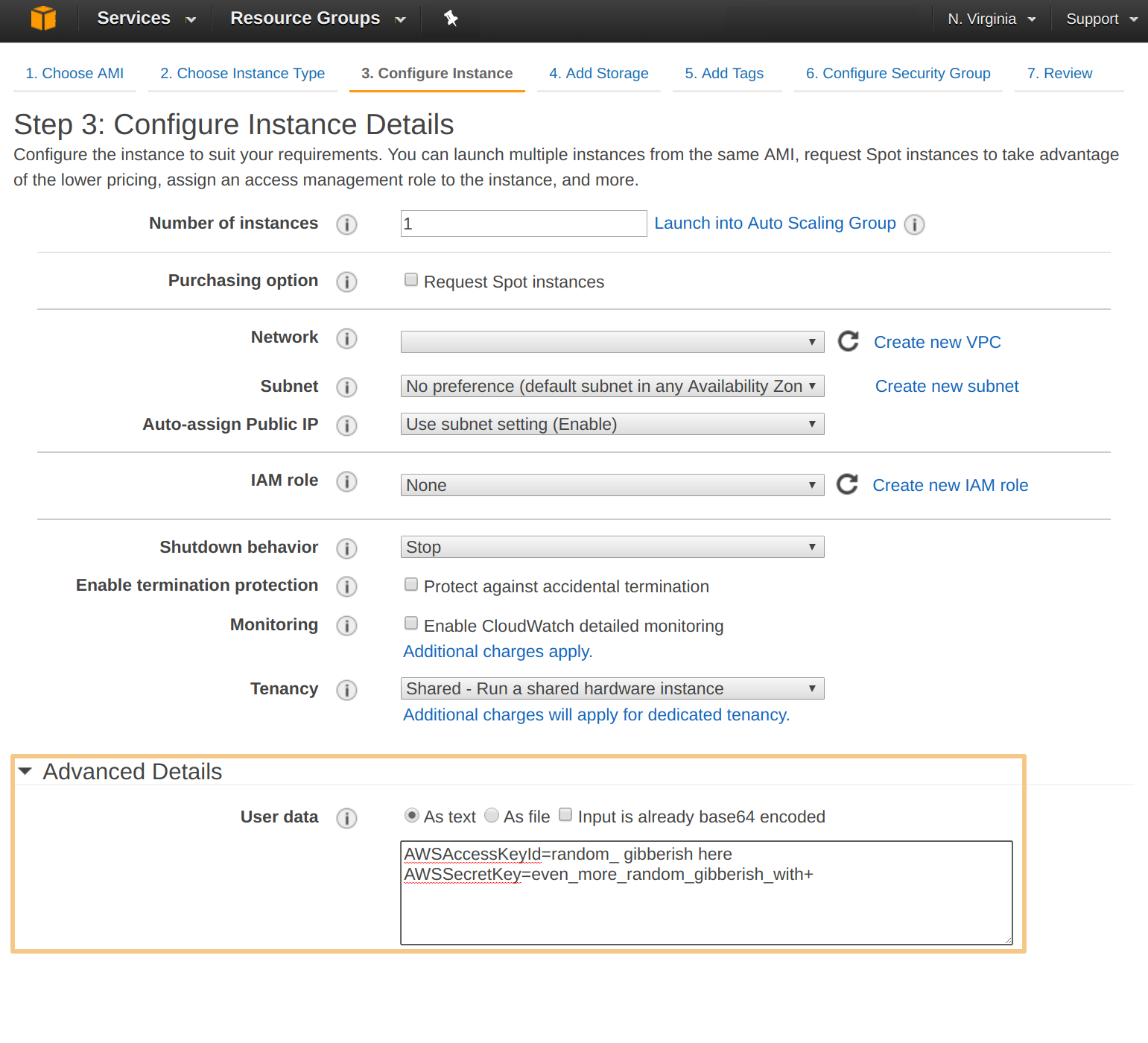
| Note: At this stage the instance can be launched and after a few minutes required to startup and subsequently exchanging the required details the IRP for Cloud will be fully operational. |
Launch IRP for Cloud satellite VM instance without an Access key
| Note: Before launching the instance prepare an Access Key. |
Launching the instance without Access Key is possible but the service will not be setup since the VM does not have the permissions mentioned above. Access keys can be provided or changed either in the CLI after connecting via SSH or in the provided configuration Web interface.
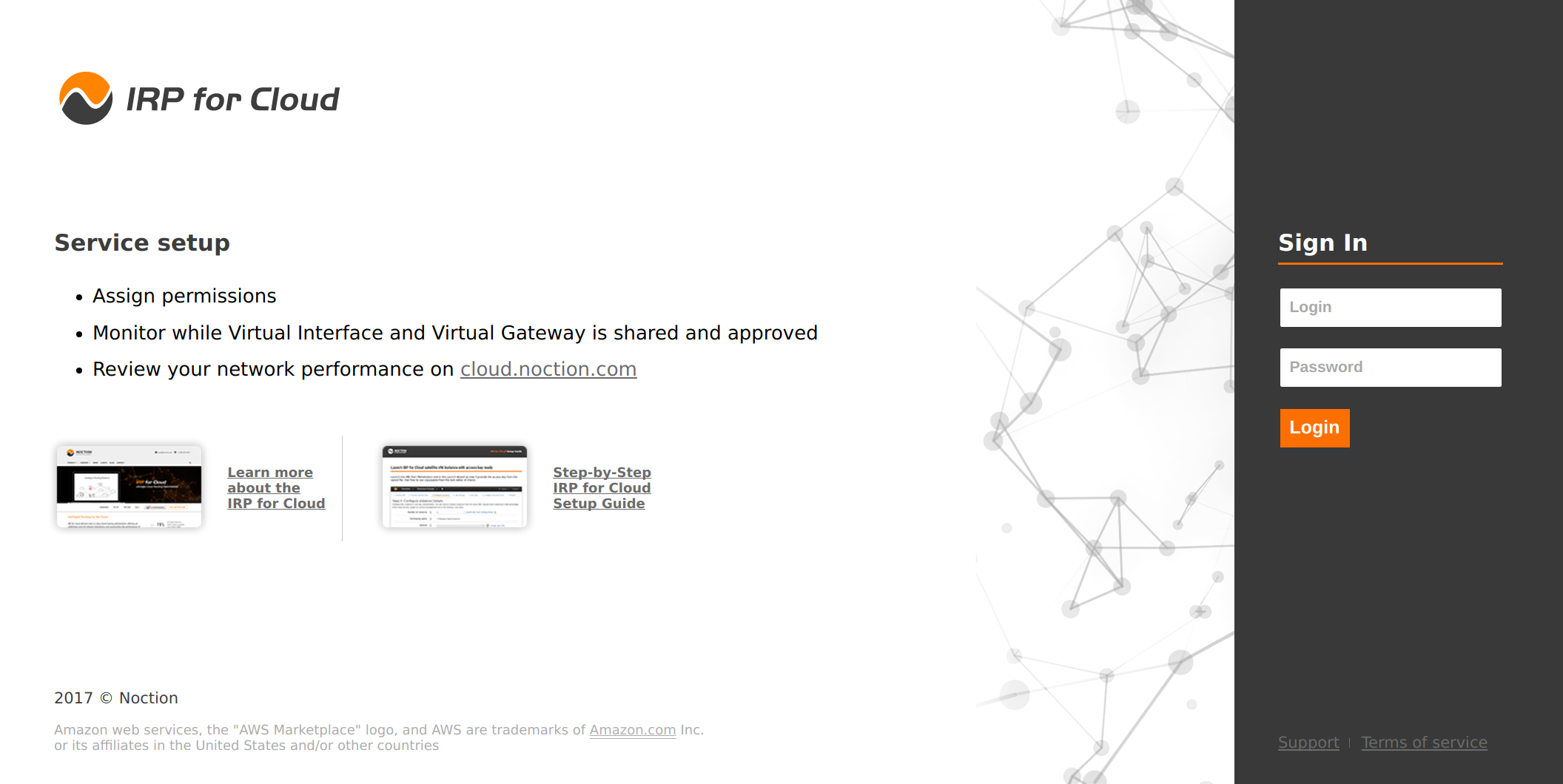
IRP for Cloud satellite VM Web interface
The satellite VM comes with a simple Web interface that displays the status of various required component of the setup and also allows setting/changing the access key.
Navigate using a web browser to the cloud provider assigned resource and login with admin/instance-id user credentials:
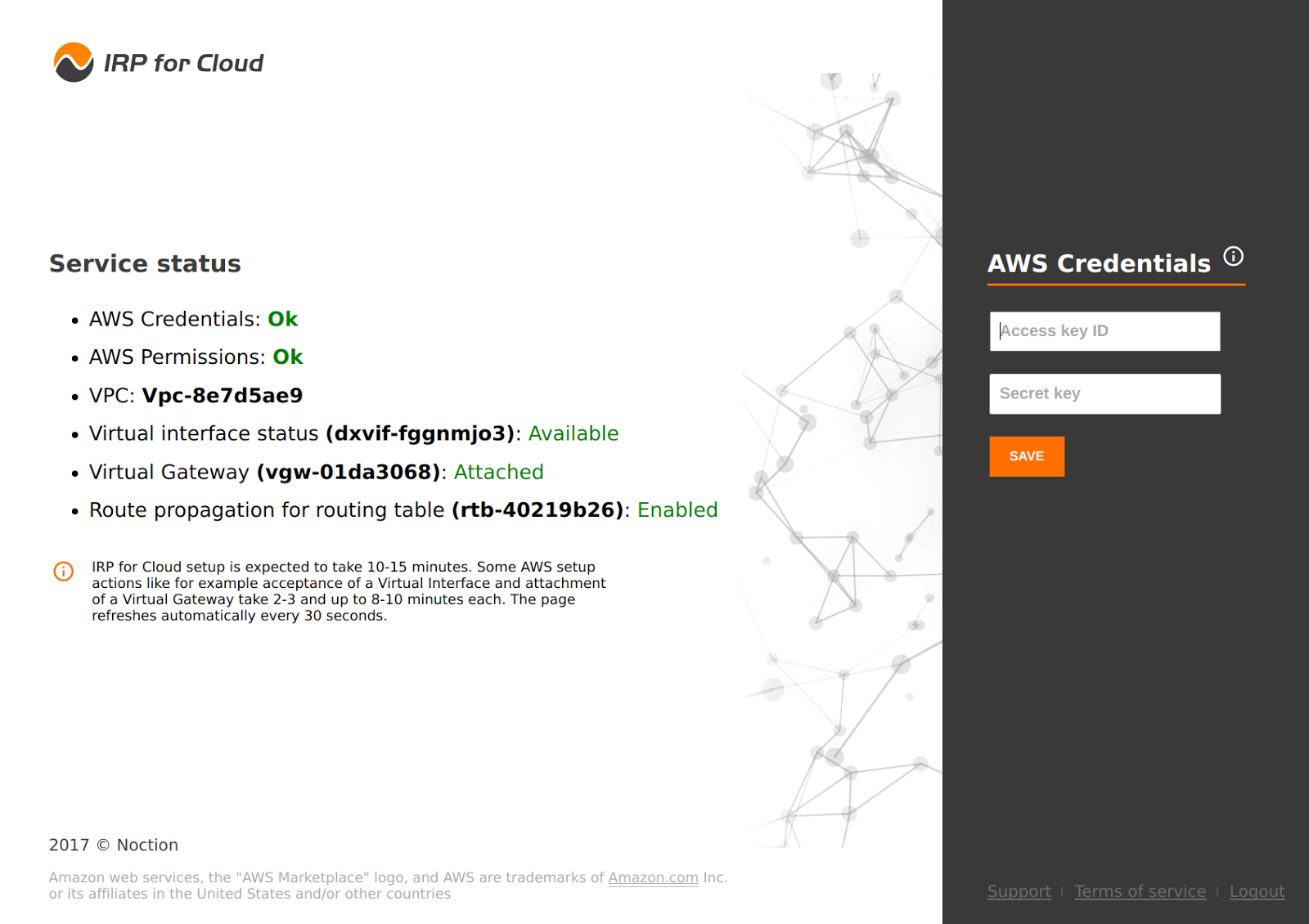
After login a similar interface will list the status of various components of the service and options to set/change the access key.
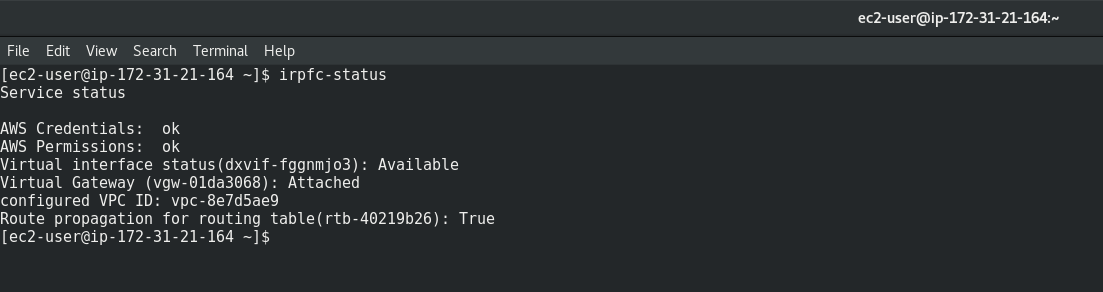
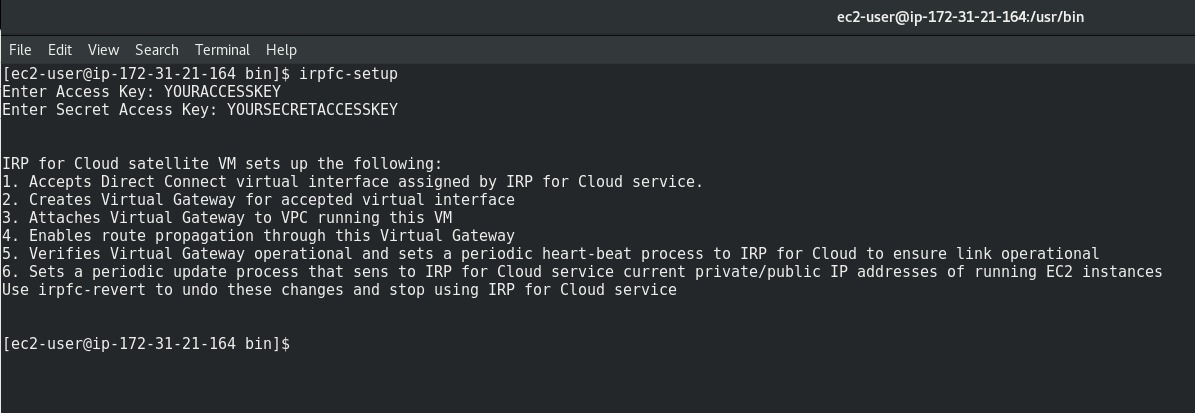
IRP for Cloud satellite VM CLI commands
You can run the following commands in your cloud provider CLI application (e.g. AWS):
IRP for Cloud Setup:
IRP for Cloud Status check: